Playing around with SAML 2.0 some more. Here is some code that I created that allowed me to create a SAML 2.0 AuthnRequest object to be submitted to an Identity Provider.
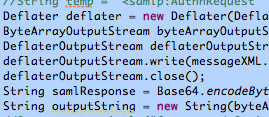
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 | public String buildAuthnRequest(){ try { XMLObjectBuilderFactory builderFactory = org.opensaml.Configuration.getBuilderFactory(); //Generate ID String randId = generateRandomHexString(42); System.out.println("Random ID: " + randId); //SAMLObjectBuilder authnRequestBuilder = (SAMLObjectBuilder) builderFactory.getBuilder(AuthnRequest.DEFAULT_ELEMENT_NAME); //AuthnRequest authnRequest = (AuthnRequest) authnRequestBuilder.buildObject(); //DocumentBuilder builder = factory.newDocumentBuilder(); //Document authXmlDocument = builder.parse(new InputSource(new StringReader(this.authRequestString))); //Create an issuer Object IssuerBuilder issuerBuilder = new IssuerBuilder(); Issuer issuer = issuerBuilder.buildObject("urn:oasis:names:tc:SAML:2.0:assertion", "Issuer", "samlp" ); issuer.setValue("http://saml20sp.abilityweb.us"); //Create NameIDPolicy NameIDPolicyBuilder nameIdPolicyBuilder = new NameIDPolicyBuilder(); NameIDPolicy nameIdPolicy = nameIdPolicyBuilder.buildObject(); //nameIdPolicy.setSchemaLocation("urn:oasis:names:tc:SAML:2.0:protocol"); nameIdPolicy.setFormat("urn:oasis:names:tc:SAML:2.0:nameid-format:persistent"); nameIdPolicy.setSPNameQualifier("http://saml20sp.abilityweb.us"); nameIdPolicy.setAllowCreate(true); //Create AuthnContextClassRef AuthnContextClassRefBuilder authnContextClassRefBuilder = new AuthnContextClassRefBuilder(); AuthnContextClassRef authnContextClassRef = authnContextClassRefBuilder.buildObject("urn:oasis:names:tc:SAML:2.0:assertion", "AuthnContextClassRef", "saml"); authnContextClassRef.setAuthnContextClassRef("urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport"); //Marshaller accrMarshaller = org.opensaml.Configuration.getMarshallerFactory().getMarshaller(authnContextClassRef); //org.w3c.dom.Element authnContextClassRefDom = accrMarshaller.marshall(authnContextClassRef); //Create RequestedAuthnContext RequestedAuthnContextBuilder requestedAuthnContextBuilder = new RequestedAuthnContextBuilder(); RequestedAuthnContext requestedAuthnContext = requestedAuthnContextBuilder.buildObject(); requestedAuthnContext.setComparison(AuthnContextComparisonTypeEnumeration.EXACT); requestedAuthnContext.getAuthnContextClassRefs().add(authnContextClassRef); //requestedAuthnContext.setDOM(authnContextClassRefDom); //authnContextClassRef. //.setParent((XMLObject) requestedAuthnContext); DateTime issueInstant = new DateTime(); AuthnRequestBuilder authRequestBuilder = new AuthnRequestBuilder(); AuthnRequest authRequest = authRequestBuilder.buildObject("urn:oasis:names:tc:SAML:2.0:protocol", "AuthnRequest", "samlp"); //AuthnRequest request = (AuthnRequest) buildXMLObject(AuthnRequest.DEFAULT_ELEMENT_NAME); //authRequest.ASSERTION_CONSUMER_SERVICE_URL_ATTRIB_NAME = "AssertionConsumerServiceURL"; //authRequest.FORCE_AUTHN_ATTRIB_NAME = "ForceAuthn"; //authRequest.IS_PASSIVE_ATTRIB_NAME = "IsPassive"; authRequest.setForceAuthn(false); authRequest.setIsPassive(false); authRequest.setIssueInstant(issueInstant); authRequest.setProtocolBinding("urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"); authRequest.setAssertionConsumerServiceURL("http://saml20sp.abilityweb.us/spdbg/sp.php"); authRequest.setIssuer(issuer); authRequest.setNameIDPolicy(nameIdPolicy); authRequest.setRequestedAuthnContext(requestedAuthnContext); //TODO: How to connect the AuthnContextClassRef that I created for this object authRequest.setID(randId); authRequest.setVersion(SAMLVersion.VERSION_20); String stringRep = authRequest.toString(); System.out.println("New AuthnRequestImpl: " + stringRep); System.out.println("Assertion Consumer Service URL: " + authRequest.getAssertionConsumerServiceURL()); // Now we must build our representation to put into the html form to be submitted to the idp Marshaller marshaller = org.opensaml.Configuration.getMarshallerFactory().getMarshaller(authRequest); org.w3c.dom.Element authDOM = marshaller.marshall(authRequest); StringWriter rspWrt = new StringWriter(); XMLHelper.writeNode(authDOM, rspWrt); String messageXML = rspWrt.toString(); //String samlResponse = new String(Base64.encodeBytes(messageXML.getBytes(), Base64.DONT_BREAK_LINES)); //delete this area //String temp = "<samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" ID="71069679271a7cf36e0e02e48084798ea844fce23f" Version="2.0" IssueInstant="2010-03-09T10:46:23Z" ForceAuthn="false" IsPassive="false" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" AssertionConsumerServiceURL="http://saml20sp.abilityweb.us/spdbg/sp.php"><saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">http://saml20sp.abilityweb.us</saml:Issuer><samlp:NameIDPolicy xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" Format="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent" SPNameQualifier="http://saml20sp.abilityweb.us" AllowCreate="true"></samlp:NameIDPolicy><samlp:RequestedAuthnContext xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" Comparison="exact"><saml:AuthnContextClassRef xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef></samlp:RequestedAuthnContext></samlp:AuthnRequest>"; Deflater deflater = new Deflater(Deflater.DEFLATED, true); ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream(); DeflaterOutputStream deflaterOutputStream = new DeflaterOutputStream(byteArrayOutputStream, deflater); deflaterOutputStream.write(messageXML.getBytes()); deflaterOutputStream.close(); String samlResponse = Base64.encodeBytes(byteArrayOutputStream.toByteArray(), Base64.DONT_BREAK_LINES); String outputString = new String(byteArrayOutputStream.toByteArray()); //System.out.println("Compressed String: " + outputString); samlResponse = URLEncoder.encode(samlResponse); String actionURL = this.redirectionUrl; System.out.println("Converted AuthRequest: " + messageXML); System.out.println("samlResponse: " + samlResponse); //messageXML = messageXML.replace("<", "<"); //messageXML = messageXML.replace(">", ">"); String url = actionURL + "?SAMLRequest=" + samlResponse + "&RelayState=" + this.relayState; System.out.println(url); return url; //HTTPRedirectDeflateEncoder httpRedirectDeflateEncoder = new HTTPRedirectDeflateEncoder(); //httpRedirectDeflateEncoder.encode((MessageContext) authDOM); } catch (MarshallingException e) { // TODO Auto-generated catch block e.printStackTrace(); } catch (UnsupportedEncodingException e) { // TODO Auto-generated catch block e.printStackTrace(); } catch (IOException e) { // TODO Auto-generated catch block e.printStackTrace(); } finally{ //Nothing yet } return ""; } |